
In this post we'll cover Savant build files and how to define your dependencies and build targets. First, let's set up a simple build file for a new project called HelloWorld. Here is how we define this project and its version:
project(group: "org.inversoft.savant.example", name: "HelloWorld", version: "1.0", licenses: ["ApacheV2_0"]) {
}
To define a project you need a group, name, version and a license. You can ignore the licenses definition for now, we'll cover that in a future post. The group name is usually a reverse DNS name (notice that the org is first not last) that identifies the owners of the project. The name is the project's formal name and the version is the project’s Semantic Version.
Next we can define the other libraries and frameworks that our project depends on. We place the dependencies inside the project definition and break them into groups. It looks like this:
project(group: "org.inversoft.savant.example", name: "HelloWorld", version: "1.0", licenses: ["ApacheV2_0"]) {
dependencies {
group(name: "compile") {
dependency(id: "org.apache.commons:commons-collections:3.1")
}
group(name: "test-compile") {
dependency(id: "org.testng:testng:6.8.7")
}
}
}
These dependency directives tell Savant that in order to compile our source code Savant needs to include Commons Collections version 3.1. Likewise, in order to compile our test source code, Savant will need to include TestNG version 6.8.7.
Continue reading →
Savant Build Tool
The Inversoft dev team is excited to announce the first preview release of the Savant build tool. Savant is written in Java and uses a Groovy DSL for the build files providing the power of the Groovy programming language for your builds.
We have been working to define the concepts of our ideal build tool for nearly a decade. By using a wide variety of other build tools including Ant, Maven, and Gradle, we have learned that dependency management, versioning and compatibility are some of the most complex problems in building software, and all of the existing build tools don’t solve these problems well. We realized that the build tool should be handling all of these concepts in the most complete way possible. To solve these problems, we adopted the Semantic Versioning standard and built Savant as a complete implementation of it.
Continue reading →
 Brian Pontarelli is a moneymaker. That’s why he is an outstanding businessman and why he was nominated for the APEX Entrepreneur of the Year award. In a time when many entrepreneurs come up with an idea, secure funding and then build a product hoping to create a market, Brian flipped the script. He built a product the market needs, secured paying customers and built a cash-flow-positive business to lay the foundation for future product development and consistent growth.
Brian Pontarelli is a moneymaker. That’s why he is an outstanding businessman and why he was nominated for the APEX Entrepreneur of the Year award. In a time when many entrepreneurs come up with an idea, secure funding and then build a product hoping to create a market, Brian flipped the script. He built a product the market needs, secured paying customers and built a cash-flow-positive business to lay the foundation for future product development and consistent growth.
A solution to a problem
Brian built the software called CleanSpeak to solve the problem of offensive and unwanted user-generated content on the Internet and then founded his company, Inversoft. This enterprise software is an intelligent filtering and moderation solution used by brands like Disney, Activision and E-Trade to protect their users online from profanity, bullying and other offensive behavior. CleanSpeak is an on-premise solution that works consistently providing the ultimate in security, performance and customizability.
Tweet this : Who needs funding? Bootstrap baby. Inversoft CEO, Brian Pontarelli Nominated ...
Continue reading →
At Inversoft, we build on-premise, enterprise software. Customers download this software and install it on their own servers. These servers might be in a cloud hosting environment like AWS or in some other datacenter somewhere.
Most of our software contains multiple components that are installed. For example, CleanSpeak has 3 separate installable applications that are shipped as RPMs, Debian packages or ZIP files. Often each of these applications are setup on multiple servers and fronted with load balancers.
We release new versions of our software every 12 to 18 months. New customers always use the latest version of our software, but current customers are never forced to upgrade. Only after 2 or 3 years do we stop supporting older versions. Once a version reaches end-of-life, bug fixes for that version are no longer done and customers on that version must upgrade to a newer version if they run into problems.
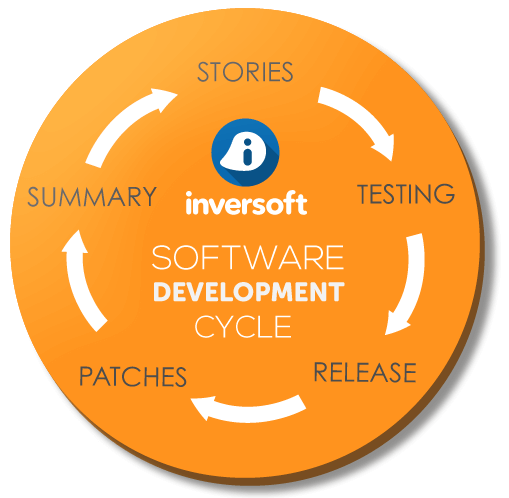 This software release model does not lend itself well to continuous deployment or fast iteration and release cycles. In fact, we have found that when we increased the frequency of our releases, customer got frustrated and annoyed, even though they were never required to upgrade.
This software release model does not lend itself well to continuous deployment or fast iteration and release cycles. In fact, we have found that when we increased the frequency of our releases, customer got frustrated and annoyed, even though they were never required to upgrade.
Keeping this in mind, let's look at how Inversoft develops and ships software.
Stories
First, we start with customer or internal requirements. We like to ensure that our features will be used and if we come up with something internally, we always ask multiple customers for input on the feature before it makes it into our product roadmap.
Continue reading →

You’ve probably heard by now that there is a serious threat to internet security. The Heartbleed bug is directly associated with the popular OpenSSL cryptographic software library. The Bug exposes secret keys used to identify service providers and to encrypt traffic, usernames, passwords and other content.
Why is it called Heartbleed?
The bug is found in the OpenSSL’s implementation of the TLS/DTLS (transport layer security protocols) heart beat extension. When exposed, memory content leaks from the server to the client and from the client to the server.
Continue reading →



 Brian Pontarelli is a moneymaker. That’s why he is an outstanding businessman
Brian Pontarelli is a moneymaker. That’s why he is an outstanding businessman  This software release model does not lend itself well to continuous deployment or fast iteration and release cycles. In fact, we have found that when we increased the frequency of our releases, customer got frustrated and annoyed, even though they were never required to upgrade.
This software release model does not lend itself well to continuous deployment or fast iteration and release cycles. In fact, we have found that when we increased the frequency of our releases, customer got frustrated and annoyed, even though they were never required to upgrade.
